Security and your online accounts

Every FI/FIRE investor, every real estate investor, and all digital nomads have their money, accounts and financial future sitting online literally behind basic passwords and maybe a single two-factor text message. Meanwhile, hackers have databases of account breaches and most every persons password(s) are somewhere in plaintext online paired with their email. That fact alone should be enough to cause concern and get you to consider upgrading your security. This article aims to be a full introduction into securing your online presence and utilizing a mix of 2FA, Biometric and U2F security. I’ll walk you through the tools, websites and practices step by step so you will be sleeping better at night knowing your finacial future is not being looted.
What is wrong with passwords and text messages?
If you google “IMSI catcher” you are going to be shocked at what you find out. In the cities and even smaller towns unscrupulous villians can, and are currently, intercepting your cell phone traffic and are able to do an attack call a Man in the middle attack which simply means, they sit in the middle and pretend they are a website and are able to hijack your session and pretend they are you. Much of this has been stymied by ubiquitous LTE and HTTPS across sites thanks to Google and Facebook, however newer “downgrade” attacks can force your phone to use non-encrypted 2G to hack you.
Google recently published a two year study called “Security Keys: Practical Cryptographic Second Factors for the Modern Web” in which they report on the findings of a rollout of security keys to 50,000 employees where they effectievly eliminated phishing attacks company-wide.
That is a really BIG deal saying that once it is set up it is not very noticeable or intrusive unless you get a new device – and even then it is quick and easy.
So, let’s see if we can do this for ourselves.
note: I use Android phones and Macbook Pro laptops so most links below will be for those, iOS and Windows typically have the same/similar apps but in their respective app stores.
Online security 101
We need to start with some terms/abbreviations, don’t worry too much about these this is more for reference.
- auth - authentication
- 1FA - One Factor Auth, just using a password to gain access
- 2FA - Two Factor Auth, two distinct ways to auth to gain access, usually a password and an OTP
- U2F - Universal 2nd Factor, simplify 2FA by tying it to trusted devices.
- WebAuthn - The backend more info
- FIDO - Fast IDentity Online, this is the specification that U2F is built on.
- OTP - One Time Password, it’s a time-based password/pin that is only good for 30-60 seconds
Before starting we should really address what we are protecting ourselves from. If you are concerned with law enforcement agencies in the United States then biometric locking your data is not a good option as it is not protected (from court order) so you should use passwords because you cannot be forced to give up a password thanks to the 5th Amendment. However, most of us here (I assume) are not spies or doing illegal stuff so we are simply concerned with protecting ourselves from hackers and from phishing scams online, both wide-net and targeted. We are trying to protect our online digital presence(s), credit ratings, bank accounts and of course our investment and retirement accounts.
So, our goal is to stop phishing and other types of attacks in their tracks and the primary online account for most people right now is a Google account. Your Google account is email for most of us and acts as a login for other sites via OAuth and even can function as a payment form, if you have an android phone then most likely all pictures you take are backed up in the cloud as well. If someone got into your Google account they could reset all your banking passwords, view any images you have, see what docs you have online and so much more.
Other accounts like twitter can also be used as OAuth general logins so we need to make sure all of them are buttoned up as well and of course we need to set maximum security preferences for all our online banking accounts.
It’s a bit of work, so let’s get started.
Step 1 - basic security
First lets secure our chrome browser so it is not an easy attack vector: do a reset and a fresh install to verify we don’t have anything bad running. Set up site isolation which protects you even if you click on a bad link.
Then install the following three extensions.
- ublock-origin - Good Ad blocker, some people also use adblock plus
- HTTPS everywhere - You want to always be using secure communication if it is available.
- Ghostery - blocks marketing and other ad trackers.
With these extension we won’t get infected with spyware or have any potential tracking and hijacking code get run in our browser.
Now you should reset your android phone (iOS) if you have any doubts, and then set up fingerprint login and an OTP auth app on your phone (see “Apps” below or use this) and then set up 2FA on every account that you have that you can think of.
- There are sites which have compiled a list of sites that support 2FA and links to directions and here is another that walks you through each site. Hint: If you use a service like Mint.com then go through all your accounts there and one by one get 2FA on them if you do not already have it.
Most banks don’t currently support U2F yet so you are going to have to max out the security offerings they do have. This means apps they have you download to your phone to work as 2FA and biometrics, some will even send you OTP devices for free. Bank of America supports fingerprint login, so do several other banks.
Going through all your accounts is a big job… I know
You might be considering stopping here, don’t, if you are then read OTP vs. U2F: Strong To Stronger
NOTE: You may also want to go through your online accounts that could have your bank account added, make sure to remove that access, so for instance if you used to use Betterment and then decided to move that money to Fundrise, then by all means disconnect Betterment from your bank because if they got hacked you had just left that there for the hackers.
Another thing to do while doing this is to modify your password recovery answers and fill them in with junk, while keeping a spreadsheet of those in Google sheets (using Google advanced protection) or on a service like Lastpass. It’s fairly easy to look up your information like your mothers maiden name or what your high school mascot was. These were never a good solution in the first place and besides its fun to make up crazy school mascots.
Step 2 - getting U2F ready
Are all of your accounts 2FA? Okay, good…
Now we get into U2F and device specific protection. If you want to dip your toe in before spending money, then I would highly suggest trying out Krypton which turns your phone into a U2F device. If you dig around with Krypton there is a wealth of great security that you can do with their command line tools, however for most users the app and Chrome extension are a fast solution to see how U2F works and it will also work with Google Advanced Protection. It might be a good idea to use the fingerprint scanner on your phone to lock it if you use Krypton. Krypton only supports a limited amount of websites right now. I personally use Krypton in conjunction with three U2F hardware keys and it’s great. To add other keys you need to turn this extension on and off, so keep that in mind if you install it.
There is a full list of sites that support (or should support) U2F and it’s a sparse list, if they don’t support it then there are links to post to social media to nag them about not supporting it.
Our goal here is to get Google Advanced Protection turned on and then secure as many of our accounts with U2F as possible.
U2F is a passwordless ‘presence check’ that proves that you are sitting there and initiated some action with a physical device. Lets look at a couple U2F login models to see how this works, the top one shows a biometric login flow and lower one shows a USB key login flow.
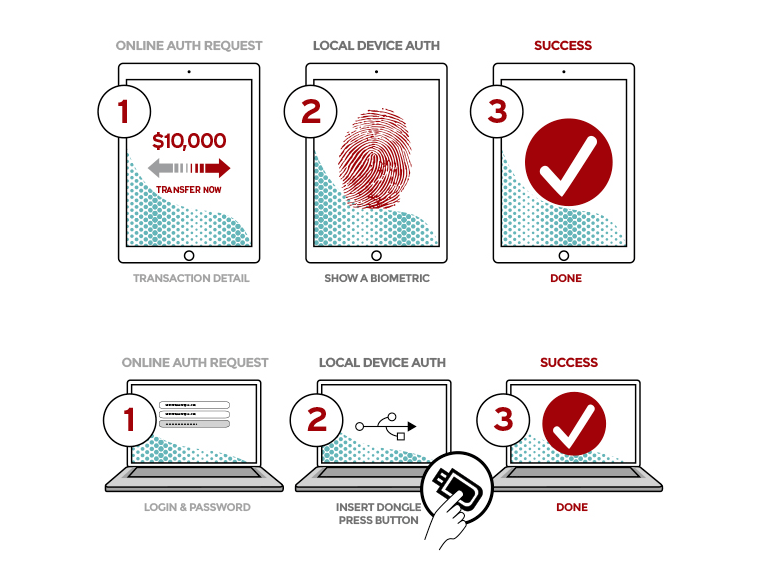
Note that you can have the option to remember a computer/phone/tablet when you do this so any subsequent logins do not require the key. This means your computer is now trusted and most all U2F supporting sites have lists of your trusted devices that you can manage.
There are a few types of U2F keys available that we can use to do Google advanced protection and the following list includes all the ones that can do NFC so you can use google on your phones and tablets. Without NFC or bluetooth your phone is not going to be happy so make sure at least one of your keys supports it.
- Google titan key bundle - $50 - Right now this is selling out faster than they can keep them in stock. It’s a multi-key with one that is BTLE/NFC/USB and another that is NFC/USB.
- Feitan bundle - $39, same thing as the Google titan bundle, if it is not available order as separate parts: multipass and epass for $41.
- Yubikey NEO - $50 NFC Yubikey, rock-solid dongle.
- Yubikey Nano - $50 Smallest of the Yubikey dongles, useful if you use your Yubikey as a partial password.
Other:
- Motiv Ring - Just announced that the $200 Motiv fitness tracker ring will support U2F. The ring supports gestures, so you can use the ‘knock’ gesture to unlock your computer and so on.
You will need at least two keys, one as your primary and one as a backup.
If you have money in Vanguard be aware that they ONLY support certain Yubikeys (Yubikey Security Key, Yubikey NEO, Yubikey 4 NANO, Yubikey 4). You will want two Yubikeys if you want to properly secure Vangaurd.
Step 3 - Lock it down.
So, you have two keys and at least one of them is a NFC or Bluetooth capable key for you phone and/or tablet. It’s now time to go to Google Advanced Protection and start the process. If you have previously added any U2F keys to Google they will be wiped out. So have two keys ready to go and follow the directions. Once you have added your keys all places you have logged into Google will be logged out, you will have log back in everywhere so get ready. Once you log back in you can add any other keys you may want to try.
Okay, so Google is locked down tight, that is the motherlode account and the one you absolutely have to keep safe. Your Google account is now secure, so be happy there. Now, lets move on and lock down our other accounts.
At the time of writing the only investment site to support U2F is Vanguard.
- Vanguard - Vanguard only supports Yubikeys but also supports biometric voice printing so when you call you are ID’d by your voice. So you have some options.
Secure up your social media, here are instructions for each.
Secure your identity providers
Okay, so now we are reasonably secure and everything won’t be a huge headache to access.
If you want to go further with security, read on.
Step 4 - additional security
We can do a few more things here with our security.
- Using a VPN is generally a good idea and using one out of your country is an even better idea if you want to make sure things are secure. You can get household routers that automatically use a VPN so you don’t have to constantly be reconnecting and typing passwords. I roll my own VPN with opensource Pritunl.
- go hardcore and install the EPIC Browser the security-first, built-in VPN browser.
- Comodo Dragon browser a well secured version of Chrome.
- Avast Online Security is a potential extension you might like to help avoid phishing and other issues if you have had problems before.
- Patch your home router! Unpatched routers being used to build vast proxy army, spy on networks
- Sign up with CreditKarma then set up 2FA and alerts on both your personal info and your credit to keep close tabs on them and be alerted on any issues.
- Switch to Signal instead of your built-in messaging.
- Use Protonmail for bank and cryptocurrency accounts that need to have extra security.
- Delete your online presence from online crawlbots that harvest infomation on people.
- Avoid downgrade attacks on your phone.
Apps and online tools
- Google Authenticator - This is basically the go-to OTP
- Authy - Similar to another app called Toopher which you tap an auth button on your phone
- MS Authenticator - Microsoft OTP
- Lastpass - Another OTP.
- LP-Password generator - nice generator for passwords.
- Keybase encrypted chat to anyone with a twitter, facebook or other social media account.
Password managers
I am very wary of password managers, they are natural magents for someone wanting full access to your life and they have proven they are not 100% secure thanks to several high profile issues so I would say go ahead and use them, but make sure to only use them in conjunction with other things mentioned here. My work also has a ‘no password manager’ rule so I don’t use them.
For the techs
This is some good stuff here.
- NFC ring you can use an imexpensive wearable NFC ring to unlock your devices.
- YubiKey-Guide - Guide to using YubiKey as a SmartCard for GPG and SSH
- Securing My Digital Life: GPG, Yubikey, & SSH on macOS using a Yubikey for a lot more that just U2F.
Cool future tech I am watching
Tokenringnot the protocol, an actual ring you wear which is a biometric and U2F device. This thing looks amazing and I will definitely be getting one.Update: Tokenring seems to not be active. If you want a FIDO2 Ring now get the Motiv since they have announced support for it.- Vue smart glasses which might have a way to tap and identify you, either way I want them.
If you have children
You want to freeze their credit, bad actors use childrens info to open fraudulent accounts at an alarming rate. First check them on acr and see if there is anything there.
- Freeze Experian for your child, mail in this form or upload docs here and then freeze it
- Equifax, first see here and then fill out the minor freeze request
- TransUnion, first check here and then submit a request here.
- If anything is at issue you need to file fraud alerts for your child, a police report and also file a complaint about it and submit a fraud report.
General security considerations
- Enable full disk encryption on your laptops
- Don’t plug things into your computer that you don’t own.
- Don’t log into any of your accounts on a device that you don’t own.
- Don’t share your passwords.
- Keep your software up to date
- Use a password manager if you want good passwords everywhere
- Don’t leave defaults on your home router.
- Set up online banking alerts to go to your phone
- Review all your privacy settings
- Make your PIN six digits long (or six points on a diagram)
- Set your phone to factory reset on 15 failed attempts.
- Backup your data
- Assume everything you post online is public.
- Consider your data retention policy, consider deleting emails older than one month in gmail
- Change your lastpass master password once per year
- Set up emergency authentication protocols with family members, if someone contacts them claiming to be you and wants money they need to absolutely verify it is indeed you.
Final thoughts
Security changes fast and with the FIDO alliance of tech giants pushing to get rid of passwords we are definitely entering a new world of personal security online. The information above is what I consider a fairly solid security plan to secure your life online and I feel it is well worth investing the time particularly if not doing something so simple could endanger your financial future.
In my case, I work for a high profile tech company, I maintain opensource cryptocurrency projects, I run multiple websites and I have been working online since the 90’s. All of these things put together means I am a juicy target and my email/pass data has shown up in multiple major hacks that have been posted online.
I hope this helps you.
NOTE:
This is a living document, I update it as I find new products.
